Recently on Facebook, my friend, nerd extraordinaire Esther Schindler, shared a photograph of herself wearing an old T-shirt and challenged her followers to identify it:
Either you have no idea what that image means, or you know exactly what it is.
It’s the torso, rolled-up sleeves and folded arms of Peter Norton, the man who was once synonymous with PC utility software, on a vintage shirt produced to promote one of his products. I found seeing him again–even without his own head–to be a surprisingly Proustian experience.
Norton was a mainframe and minicomputer programmer who bought an IBM PC soon after its 1981 release and published an enormously successful suite of software tools, the Norton Utilities, in 1982. Its killer app: UnErase, which could recover lost files back before trashcan-style deletion let you change your mind after getting rid of a file.
Norton’s empire grew to include multiple software products, articles (including a long-running PC Magazine column), and books. He was everywhere that PCs were. And then, in 1990, he sold Peter Norton Computing to Symantec, which made the Norton line of software even more successful.
After the sale, Peter Norton himself retained a high profile as a living symbol of PC maintenance; his personal brand was so powerful that it transcended his actual involvement in products which bore his name. (In the 1990s, a friend of mine wrote a book with Norton: By then, I gathered, writing a book with Peter Norton involved…well, pretty much writing a book.)
And all along, that image of a thoughtful-looking computer nerd with crossed arms was instantly recognizable. Here it is in an early incarnation, on a best-selling 1985 tome which Wikipedia informs me was known as the “pink shirt book.”
Both the formality of the necktie and the rolled-up sleeves of the classic Norton pose are meaningful. He was a pro, but he was also ready to get to work on whatever ailed your computer.
Here, on a Norton manual cover, is the folded-arm Norton as he’s remained burned into my brain all these years. (I’d forgotten that he didn’t wear glasses all along, at least when posing for photographs: Once he did, it added to his authoritative air.)
And here, in an image which I find vaguely unsettling, is a folded-arm, pink-shirt Norton in a very early (1991) ad for Norton AntiVirus, which eventually became the best-known Norton-branded product:
Esther, who seems to have done a better job of holding onto interesting computer-industry tchotchkes than I have, still has her Peter Norton Mug:
As the image below, which I borrowed from this blog post, shows, cross-armed Norton was not only iconic, but also a computer icon. (Don’t hold me to this, but I could swear that at least one version of the Norton Utilities sported an interface featuring an animated version of Peter.)
I started using MS-DOS PCs on a regular basis in 1991, and that’s when I became a user of Norton software. I was particularly fond of Disk Doctor, which repaired corrupted hard drives; and Disk Editor, which let you view and edit the data on your disk byte-by-byte. I used both of them more than once to recover from disaster, back when hard disks crashed a lot more often than they do today. I also swore by NCACHE and Speed Disk, two utilities which were superior to their Microsoft equivalents.
No disrespect meant to later, Windows-based Norton products–they’ve rescued my computer on more than one occasion–but for me, the golden age of Peter Norton’s software was when it was mostly DOS-based, lightning fast, and let you dig deeply into your computer. When Norton software switched to Windows, along with the entire utility industry, it got more bloated and tended to go after a larger, more consumery, less nerdy audience. It had less to do with the programs which Peter Norton himself had begun writing in the early 1980s. It felt less real.
Still, even in the Windows age, the crossed-arm Norton was so famous that I remembered it as appearing on all his software products and books.
Not so. Poking around the Web, I found images of him just sort of standing there (in a pink shirt), leaning on computers, hanging out with co-authors, brandishing toolboxes and hourglasses, wearing a stethoscope, and performing magic tricks with gears. And, on one particularly entertaining package, garbed in a garage-style uniform with a “Peter” label, working on a humongous floppy disk jacked up in the air.
That bottom row shows boxes dating from the turn of the century, when Symantec doubled down on Peter Norton imagery–right before it permanently removed the man altogether from product packaging in 2001. It was the end of an era, even though I’m not sure if anyone noticed at the time.
Why did Norton products no longer carry pictures of their founder? I don’t know. Maybe Symantec did extensive market testing before it made the move; maybe not.
But these later-era packages, with photos of happy, confident computer users rather than a problem-solving computer geek, hint at the company’s thinking.
I don’t care what the rationale was: Depicting someone other than Peter Norton on a Norton box was like Planters decorating a can of nuts with an anthropomorphic legume who wasn’t Mr. Peanut.
Today, Norton is probably still the best-known name in utility software; it’s even used on products for iOS and Android. But Symantec has completely disassociated the brand from Peter. Just as nobody remembers anything about Duncan Hines other than that he licensed his name to a cake-mix company, it’s possible–maybe even dead certain–that most people who use Norton products don’t have a clue who Peter Norton is.
Here’s the current Norton Utilities package, which seems particularly interested in reminding us that Symantec is the company behind Norton:
I’m glad that the Norton Utilities still exist–they even include modern versions of some of the programs I once loved, such as Disk Doctor. But so much has changed about PCs that it’s tough to remember how essential early versions of the package were. Creating a really good data-recovery program is not the road to fame and riches that it was in the 1980s.
Of course, an awful lot of people who buy Norton products these days never see a box at all. Shrinkwrapped software of the sort which once brought Peter Norton glory is largely a thing of the past; Symantec has migrated much of its line to a downloadable, subscription-based model.
Bottom line: If there’s a young Peter Norton out there today, he’s not going to become famous by appearing on utility-software boxes sold in retail stores.
As for Peter Norton himself, he may have been synonymous with PC utilities, but they weren’t his sole obsession. After selling Peter Norton Computing to Symantec, he went on to spend a sizable chunk of his loot on philanthropy and collecting modern art, two entirely admirable pursuits. I met him a few years ago when we were on a panel together, had a pleasant chat, and got the sense that he was perfectly happy not to be the guy on the software box anymore.
And yes, meeting Peter Norton did feel a little like encountering Betty Crocker or Mr. Clean in person. I hope I had the presence of mind to thank him for all the times he saved my bacon…













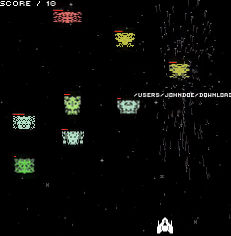 The folks at Symantec have looked right past the artistic intent behind Lose/Lose, a computer game that deletes your files every time you shoot an alien, because they’ve just classified the game as a Mac Trojan.
The folks at Symantec have looked right past the artistic intent behind Lose/Lose, a computer game that deletes your files every time you shoot an alien, because they’ve just classified the game as a Mac Trojan.

 Last week, I published the results of a little survey about Mac security that showed that the respondents, at least, are
Last week, I published the results of a little survey about Mac security that showed that the respondents, at least, are  For the past eleven days or so, I’ve
For the past eleven days or so, I’ve