 Virtually all GSM phones (such as Apple’s iPhone) and GSM wireless operators (such as AT&T and T-Mobile) on the planet appear to be vulnerable to attacks using specially crafted SMS text messages discovered by security researchers Zane Lackey and Luis Miras. At the Black Hat Briefings this morning, the two researchers demonstrated several different ways they could bypass anti-spoofing protection in cellphones, and as a result, could send phones hidden commands, profile phones, or even exploit vulnerabilities that remotely disable a targeted phone’s ability to send and receive calls or text messages.
Virtually all GSM phones (such as Apple’s iPhone) and GSM wireless operators (such as AT&T and T-Mobile) on the planet appear to be vulnerable to attacks using specially crafted SMS text messages discovered by security researchers Zane Lackey and Luis Miras. At the Black Hat Briefings this morning, the two researchers demonstrated several different ways they could bypass anti-spoofing protection in cellphones, and as a result, could send phones hidden commands, profile phones, or even exploit vulnerabilities that remotely disable a targeted phone’s ability to send and receive calls or text messages.
The researchers described how they set up test systems which could read the header data sent along with text messages, then used software to craft their own custom headers and messages and sent those messages to various types of GSM phones. Based on the behavior of the phones they tested, they were able to create several kinds of automated attacks for various phone models, and determined a method an attacker could use to silently connect to mobile phones and retrieve information that permits the attacker to identify the make and model of phone, and other profiling information.
One aspect of the vulnerability not well understood is how different models of phones will behave when they receive these specially-crafted messages. Some, like the Sony Ericsson model shown at right, provide the user no context as to whether information pushed down to the phone comes from a legitimate source.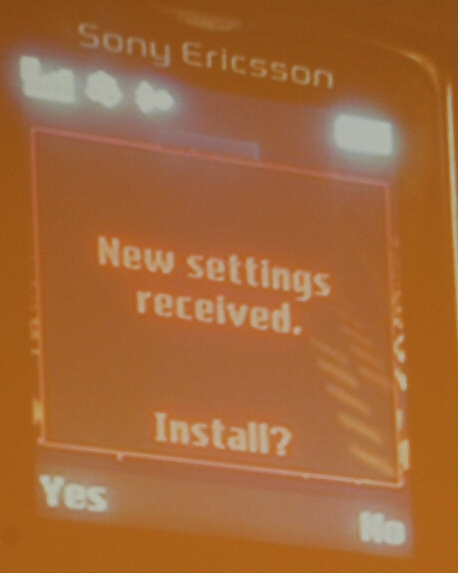
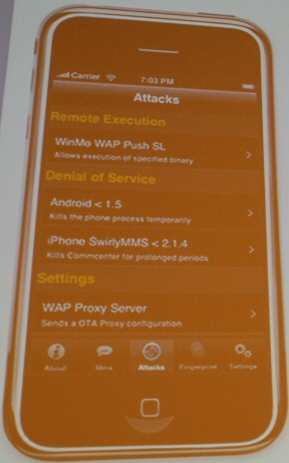
In a final coup for the conference, Lackey and Miras demonstrated an iPhone app they call TAFT which can, at the click of a few buttons, transmit various types of attacks against specific, vulnerable phone models, including iPhones, and phones running the Windows Mobile 5 and pre-“cupcake” Android operating systems.
The researchers are currently working with all major carriers and phone manufacturers to fix the problems, but warn that it may take some time before the vulnerabilities have been patched.










