![]() Twitter’s new home page, which went live yesterday, resembles a search engine, with trending topics taking the place of categories. Twitter is a useful way to learn what is happening now, but it is also a way to become quickly misinformed.
Twitter’s new home page, which went live yesterday, resembles a search engine, with trending topics taking the place of categories. Twitter is a useful way to learn what is happening now, but it is also a way to become quickly misinformed.
Social media is a nontraditional, but effective means to keep up with the day’s news and events. Event feeds, where friends share information with one another, are a much better way to stay on top of what people are talking about than e-mail ever was. I regularly check my feeds on Facebook, and to a less extent, Twitter, to stay looped in.
People that I add to my social mesh are typically people whose opinions I respect, and I find it useful to read their take on what’s happening. There is a certain amount of trust required, because status updates and tweets are not vetted sources or information (at least upfront).
Therein lies the rub. Twitter has a history of security problems and exploits, and it can be a hotbed of misinformation. In May, a rogue tweet was responsible for causing a civil rights panic, and rumors about other celebrities dying were propagated on Twitter after Michael Jackson passed away last month. The effect was viral.
Twitter is also the target of hackers. The accounts of public figures, including ABC News broadcast journalist George Stephanopoulos have been phished, and taken over by unknown persons.
The site also relies on outmoded, and easily compromised, security questions for account password retrieval.
In short, while Twitter is useful to tune into the day’s buzz, it is not a news organization. A certain degree of skepticism is required when controversial or shocking information surfaces from social media. I’m not saying that people shouldn’t use Twitter, but I am urging people to validate what they read before sharing it with others.

 Run for the hills! That’s the message iPhone owners are receiving after multiple
Run for the hills! That’s the message iPhone owners are receiving after multiple 

 How did French data thief “Hacker Croll”
How did French data thief “Hacker Croll”  at Gmail, AT&T, MobileMe, and elsewhere.
at Gmail, AT&T, MobileMe, and elsewhere.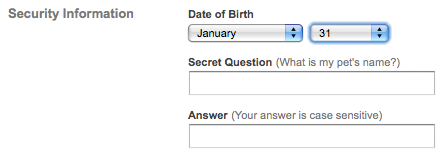
 The U.S. Court of Appeals has ruled that security software maker Kaspersky Labs had the right to label adware from Zango as malware and help PC users identify it and remove it. The ruling ends a legal battle that had been going on since 2007–part of a campaign by Zango to get off of security software’s enemies lists through lawsuits and cease-and-desist letters.
The U.S. Court of Appeals has ruled that security software maker Kaspersky Labs had the right to label adware from Zango as malware and help PC users identify it and remove it. The ruling ends a legal battle that had been going on since 2007–part of a campaign by Zango to get off of security software’s enemies lists through lawsuits and cease-and-desist letters.