For a story I wrote for SD Times, I asked leading software makers to tell me about the processes they use to develop secure software–and found that most were unwilling to discuss the subject. Some companies will provide specious reasons for not being transparent, including the notion of providing customers with “security through obscurity,’ but I believe that many are simply fearful of appearing disorganized and unconcerned.
How software is designed affects your safety, financial security, and privacy. Poorly-designed software has reportedly enabled foreign intelligence agencies to violate vital infrastructure in the United States (and presumably elsewhere), and it enables those with the know-how to get at your personal information on your own computer.
Consensus is that it is more effective to design software to be as secure as possible as early as possible in its development life cycle. Microsoft and other leading software companies have changed how they develop software to make security a requirement; consequently, vulnerabilities in Microsoft software are down dramatically.
Microsoft now shares its blueprint for developing software with its customers, and has begun to provide developers with free security tools that it uses internally. It did so because its knows that hackers are targeting applications that run on its platform, including third-party ones, as its hardens Windows with additional security.
If Microsoft is rising to the challenge, the other major software makers must be too, right? Wrong. I contacted over 20 leading companies including Apple, IBM, Nokia, Yahoo, only to be largely ignored. Include open source groups in that count. If those companies won’t be transparent, how can you trust the software that powers your cell phone, or stores your financial information?
Believe it or not, I am being told that many companies, including competitors, are asking Microsoft for advice or are simply copying its methods. That’s both encouraging and disappointing.
Some of those companies may be doing the right things, but I’m not encouraged by their silence. Software makers may do security testing after software is developed, or in bits and pieces, lacking a unified, company-wide strategy. However, security cannot be an afterthought, and there is no excuse for the industry to continue place its customers at risk.

 Poor Salma Hayek. She may be a gorgeous, accomplished, award-winning actress, but she’s apparently not very good at keeping her online accounts secure. A post at Electronic Pulp reports that
Poor Salma Hayek. She may be a gorgeous, accomplished, award-winning actress, but she’s apparently not very good at keeping her online accounts secure. A post at Electronic Pulp reports that  They’re out to get you: Sleaze balls writing devious, sneaky programs that load you system with junk. I’ll show you a few quick ways to protect yourself from Windows Trojans that want your credit card number, malware that slows your system, and spyware that tracks your keystrokes.
They’re out to get you: Sleaze balls writing devious, sneaky programs that load you system with junk. I’ll show you a few quick ways to protect yourself from Windows Trojans that want your credit card number, malware that slows your system, and spyware that tracks your keystrokes. Here’s what’s up this morning:
Here’s what’s up this morning: This has not been a good weekend at Twitter, where a series of worms has been annoying the heck out of people by infecting their accounts and sending out fake tweets under their name. The first one
This has not been a good weekend at Twitter, where a series of worms has been annoying the heck out of people by infecting their accounts and sending out fake tweets under their name. The first one 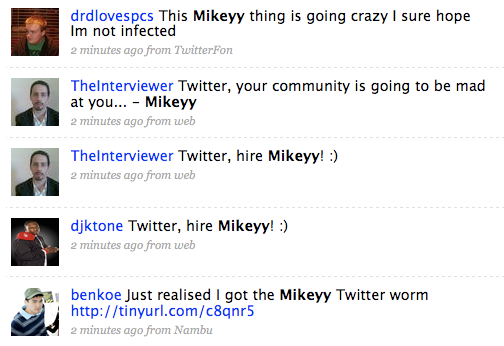
 Economic meltdown does have its downsides, but here’s one plus: massive discounts by companies hoping to attract a little attention in dire times. Check Point, the company behind the ZoneAlarm line of security software, is planning a one-day sale on its
Economic meltdown does have its downsides, but here’s one plus: massive discounts by companies hoping to attract a little attention in dire times. Check Point, the company behind the ZoneAlarm line of security software, is planning a one-day sale on its