I really hope the outrage over the TSA’s new scanners and frisking policies–and, just as important, investigative reporting like this–continues until the government has no choice but to make changes.
Tag Archives | Security
Make Yourself Invisible to Wi-Fi Hackers
 You’re at Starbucks, busy working on your Facebook page. Bad news: The guy at the next table is a hacker, and he’s also working on your Facebook page. Sit tight, I have a few ways for you to make yourself invisible to hackers.
You’re at Starbucks, busy working on your Facebook page. Bad news: The guy at the next table is a hacker, and he’s also working on your Facebook page. Sit tight, I have a few ways for you to make yourself invisible to hackers.
One Very Serious Threat
There’s a pervasive, serious Facebook and Twitter exploit that leaves you wide open to any and every hacker who can download a simple-to-use, free tool called Firesheep. It’s a threat if you’re using an unsecured, public Wi-Fi network, typically available at an Internet cafe, airport, hotel, or RV campground.
Last week TechBite paid subscribers got the first dispatch about this in the Extra newsletter; here’s a more detailed version.
Continue Reading →
11 comments
Extra Online Protection: Free, Easy, Effective
 This just in: Somebody out there is trying to trick you into clicking a link in an e-mail. Do it and you’ll be delivered to a Web site ready, willing, and absolutely able to damage your PC, steal your passwords, and use your address books.
This just in: Somebody out there is trying to trick you into clicking a link in an e-mail. Do it and you’ll be delivered to a Web site ready, willing, and absolutely able to damage your PC, steal your passwords, and use your address books.
Just this week, PandaLabs warned of a massive iTunes phishing campaign. E-mails are sent with a well-designed, authentic-looking receipt for $895. Alarmed — and unsuspecting — victims click to see how it happened and they eventually get tagged with the Zeus Trojan.
Continue Reading →
One comment
Good Grief, I Love Norton Internet Security 2011!
 On March 21, 1991, I stopped using Norton’s security programs.
On March 21, 1991, I stopped using Norton’s security programs.
But I like to see what the dark side is up to, so I recently switched back to Norton. And I’m really happy I did.
Of course, knowing how you always like to hear the dirt, I’ll tell you the back story.
It was at the March 21, 1991 user group meeting that a Norton rep was showing off the company’s latest antivirus program. “Give these a spin,” I said, handing the guy doing the demo a floppy disk filled with live viruses.
Not an unreasonable request, I thought. But that’s just me.
He avoided making eye contact, wouldn’t look at the floppy, and said “no.” That’s it. To a roomful of 350 computer users. “No.”
24 comments
Twitter’s Security Mess
Looks like I should be glad I slept in this morning: I managed to miss what sounds like a nightmarish period of worms gone wild on Twitter. (Ars Technica’s Peter Bright has a good recap of what happened, and why.) In retrospect, it looks like the culprits took advantage of a ginormous Twitter security flaw; it’s surprising it took this long for something like this to happen.
Here’s Twitter’s own account of the mess, and an apology for it.
No comments
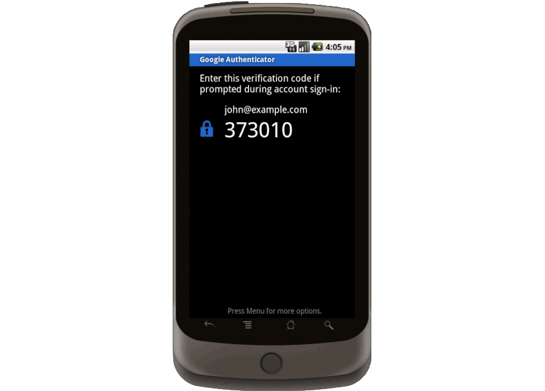
Google Apps Gets a Second Layer of Security
Passwords may be by far the Web’s most common form of security, but they’re far from airtight: some get stolen, and others are alarmingly easy to figure out. Two-factor authentication, using both a password and something else–preferably a something else that’s tough for an intruder to determine–is much safer.
So today, Google is announcing two-factor authentication for its Google Apps suite of online productivity tools. A new feature lets businesses which use Apps add another layer of security by generating random codes which employees get on their phones–Google is making apps available for Android, iPhone, and BlackBerry . To get into your account, you’ve got to enter both your password and a freshly-generated code.
The new feature is free and optional, and users who adopt it can specify certain PCs as trusted machines, permitting them to access their accounts with only a password. It’s available for paid, education, and government accounts starting today; users of the freebie Standard edition will get it “in the months ahead.”
No comments
Norton and Trend Micro Promise Less Stressful Security
 One of the biggest burdens of being a Windows user is the responsibility of protecting yourself against viruses, spyware, and other threats–attacks which increasingly aim to steal personal information and money rather than just annoy you. And one of the biggest burdens of protecting yourself from these attacks has been the degree to which security software can be problematic itself. Symantec and Trend Micro are both announcing new versions of their software today with a focus on providing security that you can welcome onto your computer–and, better yet, largely ignore once it’s there–rather than stress over.
One of the biggest burdens of being a Windows user is the responsibility of protecting yourself against viruses, spyware, and other threats–attacks which increasingly aim to steal personal information and money rather than just annoy you. And one of the biggest burdens of protecting yourself from these attacks has been the degree to which security software can be problematic itself. Symantec and Trend Micro are both announcing new versions of their software today with a focus on providing security that you can welcome onto your computer–and, better yet, largely ignore once it’s there–rather than stress over.
Symantec’s Norton products once had particularly bad reputations for being a resource-sapping, in-your-face hogs. The company has spent the past couple of years paying penance by reducing the load that new versions put on your system and the demands they place on your attention. It says that its 2011 editions are faster than both their predecessors and its competition, and that it’s reduced the number of alerts they’ll bother you with. They also snitch on other programs, via System Insight, a feature that monitors running applications and identifies ones which may be bogging you down.
4 comments
RIM Facing Government Pressure to Open Up
Press reports indicate that  BlackBerry maker RIM seems to be under increasing pressure to open up its encrypted communications from customers to governments, who are increasingly concerned about security. It seems that officials are worried that criminals — and terrorists too — are using the encryption to their advantage since there is no way to monitor transmissions.
BlackBerry maker RIM seems to be under increasing pressure to open up its encrypted communications from customers to governments, who are increasingly concerned about security. It seems that officials are worried that criminals — and terrorists too — are using the encryption to their advantage since there is no way to monitor transmissions.
The United Arab Emirates were the first to ban the devices, saying it would shut down service in October. The ban would not extend to other devices, since their digital communications pass over the open Internet. Saudi Arabia was next, who is threatening to shut off service this Friday.
Since then the list of countries with similar concerns has grown to include Kuwait, India, Indonesia, and today extended to Lebanon. While none of the countries are yet moving to ban the BlackBerry, all are asking RIM to open up.
No comments
Just How (In)secure are Smartphones?
 Last week a clever, duplicitous fifteen-year-old got Apple to approve an iPhone flashlight app which contained a secret tethering utility. A few days later, Citi told users of its iPhone mobile banking app that it was storing personal information in a manner which might have left it vulnerable to misuse by other apps or hackers.
Last week a clever, duplicitous fifteen-year-old got Apple to approve an iPhone flashlight app which contained a secret tethering utility. A few days later, Citi told users of its iPhone mobile banking app that it was storing personal information in a manner which might have left it vulnerable to misuse by other apps or hackers.
Neither incident represented a security disaster, but both provided sobering evidence that the iPhone’s level of security is less than airtight. The tethering app’s acceptance showed that it’s possible to sneak hidden code past Apple’s approval process, and the Citibank storage glitch was a useful reminder that iPhone apps aren’t completely isolated from each other.
6 comments
Apple Leads in Software (In)security
 Secunia, a security service provider well known for tracking software defects, has ranked Apple as having the most reported vulnerabilities for its platforms during the first half of 2010. The majority of the flaws reside in OS X applications.
Secunia, a security service provider well known for tracking software defects, has ranked Apple as having the most reported vulnerabilities for its platforms during the first half of 2010. The majority of the flaws reside in OS X applications.
I’m not surprised. As malicious operating systems have become more hardened, exploiting vulnerabilities has required increasingly sophisticated attacks. End users are updating their systems, using antivirus programs–at least Windows users do–and have deployed firewalls. Hackers have to look for holes in applications.
Secunia reports that vulnerabilities were found in Apple applications such as iTunes, QuickTime, and Safari, and in the apps of third parties including Adobe and Oracle. Today, we reported that Safari has a vulnerability that could allow someone to delete your address book.